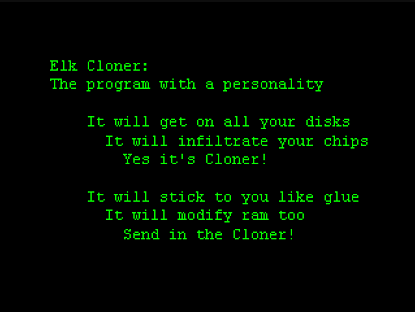
Boot Sector Virus Examples: Famous Infections Overviewed (1981-1997)
Embedded in system memory and spread via physical media, the boot sector virus has a decades-long history since the early days of computing. Boot sector viruses are especially dangerous as they seize control of the computer system before any anti-virus mechanisms can activate. Instances of this virus type have variedRead More →